The number of data breaches and exposed records in the U.S. has reached the highest figures to date in 2017. While practically every CMS talks about the scalability and user experience, security still remains a critical component that doesn’t get as much air time as it should.
Drupal has a reputation when it comes to security. According to 2017 Sucuri hacked website reports, Drupal is one of the least infected CMS for that year.
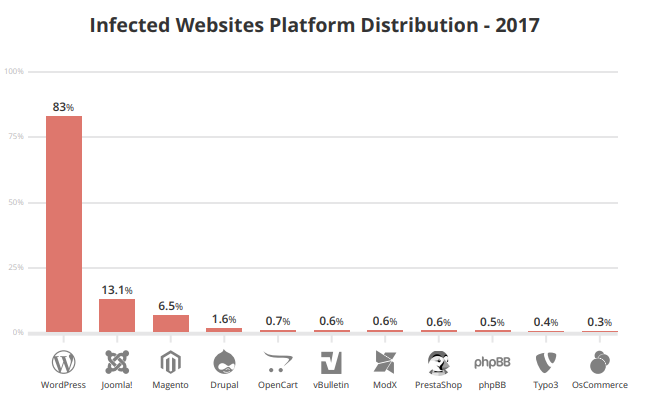
Source: Hacked Website Report 2017 Statistics
Several government, educational, and global enterprises are opting for Drupal for its security, and content management. Taking a look at Drupal’s top security modules:
Top Drupal Security Modules
Challenge Response and Spam Detection Modules
Challenge–response authentication is a protocol where the user is presented with a question. Failing to provide the right answer, the user may be debarred from accessing the website.
We all have come across the captcha response which ensures that the spambots are filtered out. Here are the top challenge-response and spam detection modules:
1. Captcha: A challenge-response test, which is often placed within the web forms to determine whether the user is human. The purpose of CAPTCHA is to block form submissions by spambots. The module provides this feature to virtually any user-facing web form on a Drupal site.
2. reCaptcha: Using Google reCAPTCHA web service, the module helps to improvise the CAPTCHA system. It helps you detect abusive traffic on your website without any user friction.

3. Spamicide: It aims to prevent spam submission to any form on your Drupal website. Spamicide adds an input field to each form then hides it with CSS. When spam bots fill in the field, the form is discarded.
The field, and matching .css file, are named in such a way so as to not let on that it is a spam defeating device, and can be set by the admins to almost anything they like. It can also show if and when a particular form has been compromised, allowing the admin to change the form's field name (and corresponding .css file) to something else.
4. Honeypot: It uses a method to inculcate a fake input field into the form which is only visible to the bots. Honeypot uses both the honeypot and timestamp methods of deterring spam bots from completing forms on your Drupal site.
The module currently supports all forms on the site, or particular forms like user registration or password reset forms, web forms, contact forms, node forms, and comment forms.
5. Antibot - An extremely lightweight module designed to eliminate robotic form submissions, Antibot works completely behind the scenes and doesn't require any interaction from the end-users (no annoying CAPTCHAs!) with an exception to enabled Javascript.
“In case your website is built on Drupal 8 you can use up to 187 modules".
Authentication Module
A number of systems have been developed that allow domain name owners to identify an email address as authorized. While not directly attacking spam, these systems make it much harder to spoof addresses, a common technique of spammers.
6. Oauth - Providing a method for clients to access server resources on behalf of a resource owner (such as a different client or an end-user). OAuth provides a process for end-users to authorize third-party access to their server resources without sharing their credentials (typically, a username and password pair), using user-agent re-directions.
7. LDAP - The Lightweight Directory Access Protocol (LDAP) provides authentication, user provisioning, authorization, feeds, and views.
8. Secure Login - For sites that are available via both HTTP and HTTPS, Secure Login ensures that the user login and other forms are submitted securely via HTTPS. It helps prevent passwords and ther private user data from being transmitted in the process.
The module locks down not just the user/login page but also any page containing the user login block, and any other forms that you configure to be secured.
Secure Login module enforces secure authenticated session cookies, thus preventing session hijacking by eavesdroppers.
9. SimpleSAML - This module integrates Drupal with SimpleSAMLphp, the most robust and complete implementation of SAML in PHP. It makes it possible for Drupal to communicate with SAML or Shibboleth identity providers (IdP) for authenticating users. The resulting Drupal site can effectively act as a SAML or Shibboleth service provider (SP).
Password
Repeatedly using the same or 'weak' passwords can leave you vulnerable to hackers. If the password is hacked, your personal and sensitive information could be prone to misuse.
10. Password policy - A password policy can be defined with a set of constraints which must be met before a user password change will be accepted. Each constraint has a parameter allowing for the minimum number of valid conditions which must be met before the constraint is satisfied.
11. Encrypt - With an API for performing symmetric encryption, Encrypt allows encryption and decryption of data in a standardized manner. Aside from administration pages to manage encryption profiles, it supports a variety of ciphers for strong encryption.
Admin and User Security
Users, roles and permissions are key components of website security, and they're of major importance in Drupal as well.
12. Admin per menu - Users with no admin access will, by default, not be able to see the menu item. Drupal allows only users with the Administer menus and menu items permission to add, modify or delete menu items, thus preventing the possibility of accidents and security breaches.Menu Admin per Menu allows giving ‘roles per menu’ admin permissions without giving them full admin permission.
13. Username Enumeration prevention - There is a way to exploit the system by using a technique called username enumeration. By using the forgot password form and a technique called “username enumeration”, the attacker can enter a username that does not exist and they will get a response from Drupal saying so.User Enumeration Prevention prevents this from happening.
When the module is enabled, the error message will be replaced for the same message as a valid user and they will be redirected back to the login form. If the user does not exist, no password reset email will be sent, but the attacker will not know this is the case.
14. Key - Empowering the site administrator by letting them define how and where keys are stored, Key elevates the security by meeting the regulatory requirements. In the end, it ensures that sensitive keys (encryption keys and API) are managed and security is improved.
Miscellaneous
While the above mentioned modules cover the majority of the security modules, here are some more you can use:
15. SecKit - SecKit provides Drupal with various security-hardening options. This lets your mitigate the risks of exploitation of different web application vulnerabilities.It secures the site from cross site scripting, click jacking, cross site request forgery, and SSL/TLS.
16. Persistent login - The Persistent Login module provides a "Remember Me" option on the user login form. Persistent Login is independent of the PHP session settings and is more secure (and user-friendly) than simply setting a long PHP session lifetime.
17. Mime detection - MimeDetect provides a complete system for detecting the actual content of files in your Drupal site.
By default, Drupal provides a "guessing" system based on the filename extension. This is very weak and your site could store files with real content different from the one indicated by its extension.
18. Paranoia - The Paranoia module attempts to identify all the places that a user can evaluate PHP via Drupal's web interface and then block those. It reduces the potential impact of an attacker gaining elevated permission on a Drupal site.
The specific features are:
-
Disable granting of the "use PHP for block visibility" permission.
-
Disable creation of input formats that use the PHP filter.
-
Disable editing the user #1 account.
-
Prevent granting risky permissions.
Looking for better security options? Drop us a line and our Drupal experts will be in touch.
Our Services
Customer Experience Management
- Content Management
- Marketing Automation
- Mobile Application Development
- Drupal Support and Maintanence
Enterprise Modernization, Platforms & Cloud
- Modernization Strategy
- API Management & Developer Portals
- Hybrid Cloud & Cloud Native Platforms
- Site Reliability Engineering