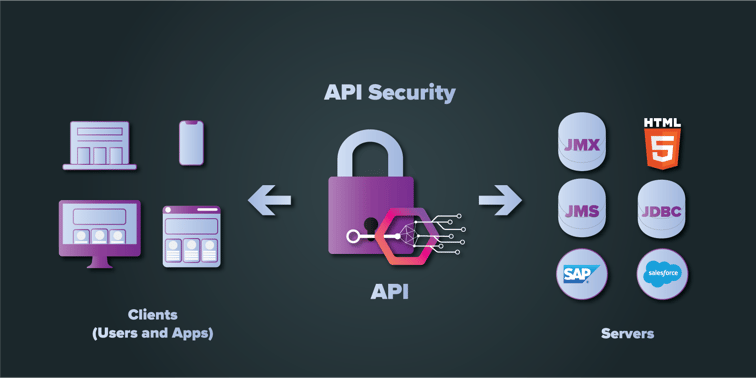
APIs have undoubtedly redefined the architecture of the digital ecosystem. From seamless integration of features across web products to leveraging the creative liberty to developers, there is so much more which is yet to be discovered and developed.
APIs have evolved as the superpower that helps businesses rule their markets by winning their customers’ hearts. And when we talk of such quantum of power and command, we should not forget what Uncle Ben told Peter Parker - ‘with great power comes great responsibility’; which, quite accurately, is applicable to APIs.
In this blog we will discover the challenges, needs and the best practices around API security that will help you take a step towards a secure, stable and profitable API model.
Oh API! Why so Mysterious?
With the majority of web products relying on API, the need for security is higher than ever because APIs handle a huge amount of sensitive data. Traditionally, web security has not been an easy task and this holds true even for APIs. This world of microservice architecture is even more complex and difficult to decode than the existing web world.
Cost of fixing an API bug can be 2x fixing the bug for traditional web services
More often than not the level of complexity is directly proportional to the cost associated with the security. Independent researches quote that the cost of spotting and fixing an API bug can be as high as 1.5 or 2x of fixing the bug for traditional web services.
Moreover, even though there are common design threads that are applicable across multiple APIs, each architecture works differently. Although even after so many hurdles, API security is too valuable to be compromised with, a minor security snag can lead to serious data breaches and can even render the API and the application completely useless.
Another major snag that hits API security is a lack of responsibility. A recent Ovum study reveals that about 50% of respondents believe that the IT department is responsible for securing the APIs while the rest believe this responsibility lies with the API development team. With this huge parity of understanding, API security is bound to fall through cracks. As a matter of fact, the security doesn’t begin or end at the developer’s hand. Rather it involves everyone, from developers to consumers. So, compiled below is a list of best practices that should be incorporated within the API to ensure that the basic security structure is in place.
The security doesn’t begin or end at the developer’s hand, it involves everyone
Best Practices too Valuable to be Ignored
- Mapping Attack Possibilities
One of the easiest ways to be attacked and being reduced to nothing is being oblivious to the possibilities that need to be covered. Unless the business analyses what is exposed, one cannot define the actual levels of vulnerability of the system, which is the foundation of API management. Establishing visibility contributes to strengthening the systems as it can fetch answers for questions like: What can be inferred from the traffic abnormalities? Are anomalies always an indicator of attacks? What is the frequency of these attacks? Who are the repeated offenders of such abnormalities? Etc.
What pitches the game a notch higher is the ability to access it real-time. For example, if the security team is able to spot a case of DoS, it can prevent the API from failing and thus satisfies the users and keeps up the online services. This aspect also contributes to the fact that APIs are not just a mere component, but the backbone of the business.
- Implementing Stringent Authentication Measures
A secured API provides authentication on both the ends, that is, the user and the application. And with such a need, it is absolutely impossible to not mention OAuth2. It enabled a limited and time-bound access to the user without revealing any data. For APIS, such a method is called a token-based authentication and authorization. The client is allowed to make an API call to exchange the credentials for a token, which in turn gives it access to API.
This can be explained via a simple scenario wherein a user tries to login to another platform. In such scenarios OAuth2 is mostly utilized to grant access to the user but the password is secure and not revealed to the other platform. The transaction is facilitated using a token, but without revealing the password. So, even in the case when the platform (or client) is compromised, it cannot leak the key information such as passwords.
- Input Validation
This enables the application to validate the user inputs with the defined parameters. This has proved to be one of the best defences against the injection attacks, cross-site scripting, and other such common threats. So, to begin with a well-defined process, the APIs should utilize well-defined specifications or can even deploy a shared library to achieve consistency.
There are two advantages of this protocol, firstly, you get to filter out the malicious attacks and secondly you can seamlessly identify who are the most dubious cases. In general, cyber thieves follow a pattern of venturing one parameter after other, in order to explore any scope of security snag. Leveraging input validation, businesses can identify such potential bad actors.
- Beat the Bot
By now, we have established that greater the number of branches of digital automation, higher will be the number of threats. Well, this can be worn as a badge of honour by businesses for truly transforming into the digital landscape.
Of many such attacks and vulnerabilities, bots play a major role. Attacks like DoS are carried out by an army of bots and across the internet, there are multiple examples of things as such.
However, instead of falling prey to such hurdles, these can be utilized for a bigger purchase – traffic management and analysis. Adding something as basic as a reCaptcha can be really helpful, while it might be a temporary inconvenience for an authentic user, to bots it is something much greater to deal with.
-
Encouraging Self-Reliance
Nothing beats attackers and intruders than a well-equipped system. As discussed before, a better visibility will empower your team to perform better. One of the best ways of doing so is a self-developer portal.
While the businesses can control the amount of data visibility to the users, the users can begin experimenting with the APIs. At the same time it will open up more avenues for monetization as well.
These metrics can be analysed to again check for authentic users as well as attackers. This equips the businesses and at the same time helps them save an authentic user from an impending attack.
These best practises do quite well in promoting the security of your API system. But it should not be forgotten that each business requires its own unique strategy. Simply pushing one standard solution set to a problem may not work and yield disastrous results.
So, businesses should work on developing a solution set that – analyses the problem, one set at a time – deploys cross-functional teams to fix it – and then moves on to the next problem. Following a self-tailored approach greatly reduces the possibility of complete lockdown of the system and is accessible to others. Having said that we would like to conclude with the fact that the API traffic is not just for capitalization but also defining authenticating users and driving higher levels of security by eliminating the bad actors.
Our Services
Customer Experience Management
- Content Management
- Marketing Automation
- Mobile Application Development
- Drupal Support and Maintanence
Enterprise Modernization, Platforms & Cloud
- Modernization Strategy
- API Management & Developer Portals
- Hybrid Cloud & Cloud Native Platforms
- Site Reliability Engineering